Pentagon Sounds Retreat on CMMC Compliance
The Defense Department has rolled out a new version of its CMMC program for cybersecurity compliance for defense contractors, dropping requirements for many defense contractors to get outside assessments of their cybersecurity and giving the Pentagon more discretion to waive security requirements for the rest.
The changes, announced Thursday afternoon, are a climb-down from the original CMMC program unveiled in early 2020. That program established five levels of cybersecurity, and contractors would need to achieve increasingly higher levels of security depending on the importance of the defense projects they were working on. Contractors would also need to obtain certification from approved, independent third-party assessors. The goal was to have the entire defense industrial base in compliance with CMMC by 2026.
Well, that’s out the window. The new “CMMC 2.0” program has only three levels of security, and defense contractors in the first two tiers will be able to self-certify their own cybersecurity programs. Pentagon officials will also be able to waive cybersecurity requirements “under certain limited circumstances” for “selection mission-critical requirements.” Figure 1, below, shows the major changes from CMMC 1.0 to 2.0.
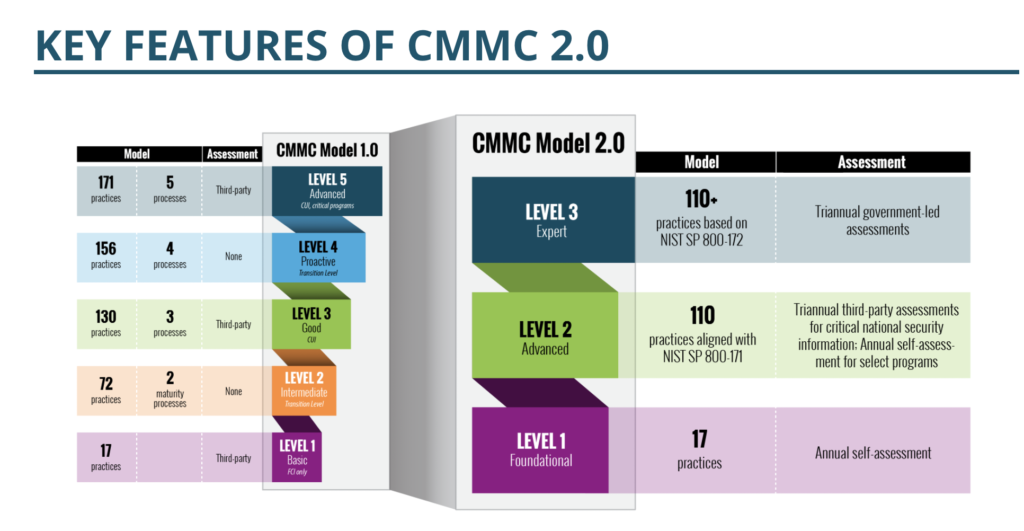
Source: Defense Department
Oh, and the pilot program to begin CMMC this year with large defense contractors is also suspended pending further rulemaking.
Defense contractors will still need to implement security controls according to the NIST 800-171 standard. Under CMMC 2.0, however, the Defense Department will only require that contractors have a certain number of baseline controls in place when the contract is awarded; companies will be allowed to implement the remaining controls sometime in the future under a Plan of Action & Milestones. The original CMMC program expected all controls to be in place at the start of the contract.
In one of the more eye-rolling attempts at bureaucratic doublespeak, Jesse Salazar, deputy sssistant secretary of defense for industrial policy, said CMMC 2.0 “will dramatically strengthen the cybersecurity of the defense industrial base. By establishing a more collaborative relationship with industry, these updates will support businesses in adopting the practices they need to thwart cyber threats while minimizing barriers to compliance with DoD requirements.”
TL;DR — defense contractors pushed back against the Defense Department’s security demands, and the department reversed course.
The CMMC Retreat Should Not Be a Surprise
Whatever the need for stronger cybersecurity in the defense sector, the original CMMC program did have its drawbacks. The defense sector never had anywhere near an adequate number of third-party assessors to review cybersecurity, and implementing NIST 800-171 (especially the part about maintaining control over sub-contractors in your supply chain) is no easy feat.
Moreover, businesses had been pooping on CMMC’s compliance burdens since the original plans were unveiled last year. So, as with so many other cybersecurity ambitions we’ve seen over the years, the feds watered down their demands to something more palatable to corporate interests. Readers can decide for themselves, both as compliance professionals and as Americans, whether this move makes sense.
Coincidentally, the Biden Administration issued an order just yesterday to federal agencies that they must patch hundreds of security flaws in government software systems immediately.
Also coincidentally, I just finished the book This Is How They Tell Me the World Ends, an excellent history of the cyber-weapons arms race around the world, written by New York Times reporter Nicole Perlroth. She paints a truly frightening picture of how vulnerable the world’s critical infrastructure is to cybersecurity attackers.
OK, now decide how wise this CMMC 2.0 idea is.
